Article de blog
Election Cybersecurity Congressional Briefing: Facebook Live Recording
 Editor’s Note: The briefing was live-streamed on Facebook Live and is available on the Common Cause Facebook page. Don’t forget to “like/follow” us while you’re there.
Editor’s Note: The briefing was live-streamed on Facebook Live and is available on the Common Cause Facebook page. Don’t forget to “like/follow” us while you’re there.
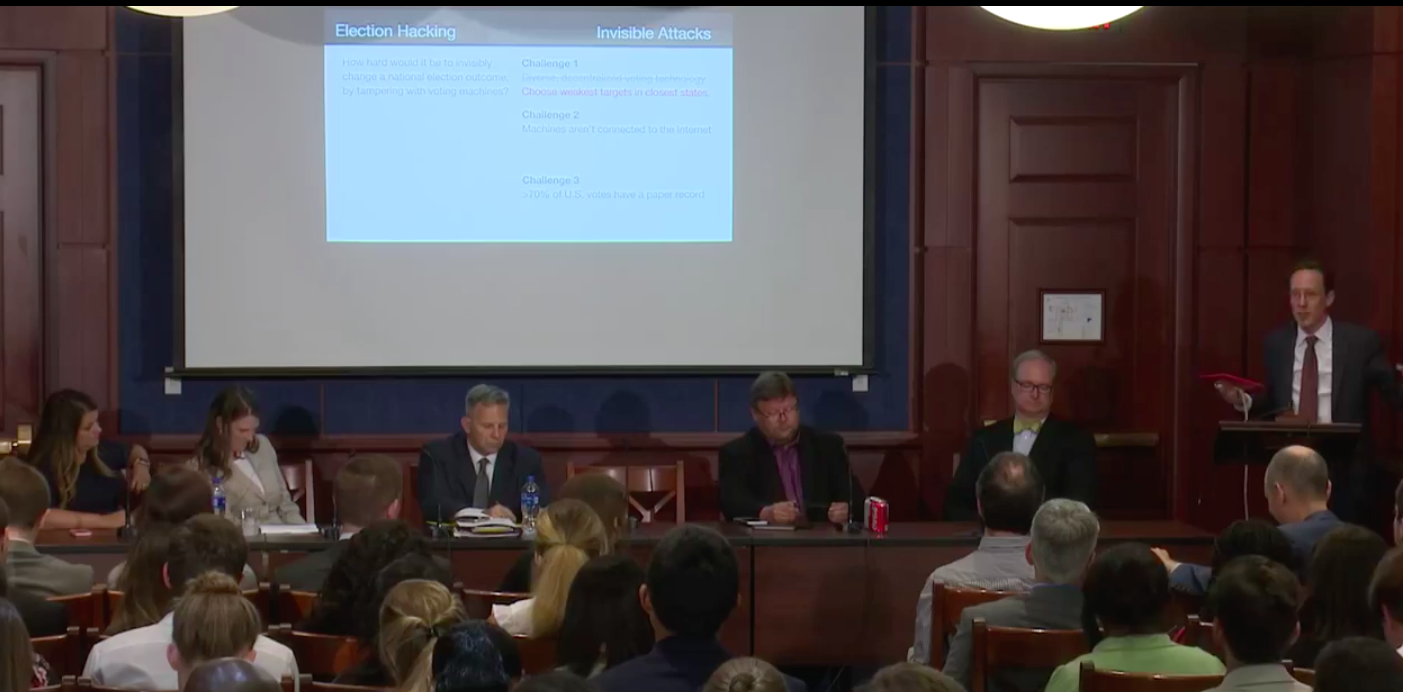
Hacking the average voting machine is not hard. In fact, every voting machine used in the United States that has been tested is easily hackable. Low barriers to entry make becoming a hacker easy. The tools needed cost under $100, and the know-how can be obtained by watching YouTube videos.
Across America, there are 18,000 diverse voting districts, all of which independently choose their voting systems. This serves as both a strength, in that to compromise the entire system would be a difficult operation, but also a weakness; swing states with the weakest protections could be targeted more directly.
Voting machines do not have to be connected to the internet, because their software usually is connected before being downloaded to the machine. There are several ways a hacker can do damage, including but not limited to: (1) altering after-election results, by hacking into reporting systems, (2) sabotaging registration records to create long lines and confusion at polls, and (3) silently infecting voter machines with malicious software that directly alters the vote record.
It’s not all doom and gloom; there are solutions at work. The consensus is that paper ballots and post-election audits are pragmatic solutions to preventing election hacking. Auditing can be costly, but it Risk-Limiting Audits (RLAs) have become a popularly cost-effective way to achieve 95%+ confidence levels in the accuracy of elections. RLA is taking a sample of the paper ballots and counting them by hand, and the size of that sample increases with the closeness of the election.